On December 26, 2023, the much-anticipated proposed rule codifying the Cybersecurity Maturity Model Certification (“CMMC”) 2.0 process was released for public comment. Commenters have until February 26, 2024, to provide input on this proposed rule.
This proposed rule reflects many changes already anticipated by the government contracting community. As expected, CMMC 2.0 uses three levels, not five, to implement the required security measures for handling Federal Contract Information (“FCI”) and Controlled Unclassified Information (“CUI”) which in turn requires implementing the security standards set forth in National Institute of Standards and Technology (“NIST”) Special Publication (“SP”) 800–171 Rev 2 and NIST SP 800–172 as applicable, including any plan of action and milestones (“POAMs”) documenting any requirements not yet implemented.
Here are the key features of CMMC 2.0:
- For CMMC Level 1, contractors must verify annually through self-assessments entered into the Supplier Performance Risk System (“SPRS”) that all applicable security requirements outlined in FAR clause 52.204–21 have been implemented. Annual certifications must then be affirmed in SPRS by a contractor’s senior official.
- For CMMC Level 2, contractors must verify tri-annually through self-assessments or a third-party certification assessment (from a third-party certifier, i.e., a C3PAO) entered into SPRS that all applicable security requirements outlined in NIST SP 800–171 Rev 2 and required via DFARS clause 252.204–7012 have been implemented. Annual, continuing compliance, and POAM closure certifications must then be affirmed in SPRS by a contractor’s senior official.
- For CMMC Level 3, Department of Defense (“DoD”) assessors must implement and verify every third year through DoD’s Enterprise Mission Assurance Support Services (“eMASS”) (which communicates with SPRS) that contractors meet and have implemented all applicable security requirements from NIST SP 800–172. Annual, continuing compliance, and POAM closure certifications must then be affirmed in SPRS by a contractor’s senior official.
CMMC 2.0 applies to all DoD government contractors, including prime and subcontractors (no matter how remote a contractor’s work on an implicated government contract is) that will process, store or transmit FCI or CUI information on the contractor’s information systems. It does not apply to those that operate government information systems on behalf of the government.
There are limited exceptions: (1) the commercial-off-the-shelf (“COTS”) exception1; (2) purchases below the micro-purchase threshold (currently $10,000 in most cases); and (3) when the contracting office requests a waiver for part or all of the CMMC requirements. Notably, there is no small business exception, and contractors may not request their own waivers.
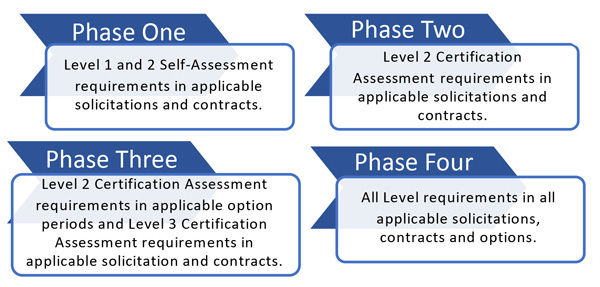
While the three exceptions provide relief to a small subset of the government contracting community, others will have to ready themselves for full compliance, expected by October 1, 2026. The CMMC 2.0 Levels 1 through 3 are being rolled out in a four-phase approach depicted here:
- Phase One: Begins on the effective date of revision to DFAR Section 252.204-7021 to include the assessment requirement as a condition of contract award.
-
Phase Two: Begins 6 months after the start of Phase One.
-
Phase Three: Begins one year after the start of Phase Two.
-
Phase Four (Full Implementation): Begins one year after the start of Phase Three.
We will continue to monitor the advancement of the CMMC 2.0 phases beginning with the promulgation of DFAR 252.204-7021 changes.
New Year Resolutions: Four Actions you can take in 2024
Given the demands of CMMC 2.0 and anticipated timeline, we recommend that non-excepted contractors continue to take action now to achieve compliance in time for when the requirements take full effect.
- Survey your industry to determine whether your government contract opportunities are likely to require Level 2 and up (i.e., are you likely to handle CUI). If so, then you may have to secure a third-party certification (from a C3PAO certifier) in lieu of self-certification under a Level 2 requirement for which self-certification is not guaranteed. Review the current CUI categories here.
- Continue to review the NIST SP 800-171 Rev 2 documentation which covers the most frequently encountered CMMC Level 2 requirements for the handling of CUI. We have yet to see whether DoD’s Chief Information Officer (“CIO”) will push for CMMC requirement updates based on the recent Revision 3 changes published for public comment through January 26, 2024.
- Review the previously released CMMC 2.0 Assessment Guides. Future updates to CMMC guidance may come as needed and as the proposed rule is finalized. Continue to check the DoD CIO website for those updates.
- Continue to document any POAMs you intend to establish in lieu of full compliance prior to the implementation date, bearing in mind that all POAMs must be closed within 180 days of the initial assessment.
Remember, that if you have already achieved FedRAMP compliance, you are already on your way to achieving CMMC 2.0 compliance. In this case, your immediate actions should also include conducting a gap analysis to determine where there are compliance holes from FedRAMP compliance you can work toward closing.
The Morris, Manning & Martin, LLP Government Contracts team continues to closely track cybersecurity updates including developments to CMMC 2.0 post-comment period and is available to advise clients as the compliance regime continues to shift and develop.
1 For the COTS exception to apply, the contractor may provide only COTS items under the government contract incorporating CMMC 2.0; it cannot also provide services ancillary to the COTS products.



